More Hardware: LetsTrust-TPM2Go
2023 August 8th,
Finally shipped to the stock \o/.

I hope, you will find this USB-Stick useful for your development!
Bye,
Paul
2023 August 2nd,
Update:
Shipment will start next week! \o/
Hello and welcome back,
Today, I would like to introduce my new product: LetsTrust-TPM2Go!
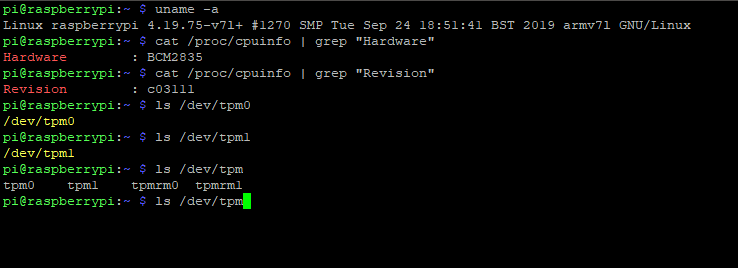
LetsTrust-TPM2Go is a USB 2.0 stick with a built-in TPM. It is designed to be compatible with Linux PCs or single-board computers that have USB-A ports (probably macOS but I could not test it). This product's main purpose is to simplify application development with TPM support. It can also be used if your embedded device is not ready or only has free USB ports on your target device.
Windows 11: LetsTrust-TPM2Go USB Stick is NOT compatible with Microsoft Windows 11 TPM 2.0 requirement!
Windows 10: LetsTrust-TPM2Go is not compatible [1].
Features:
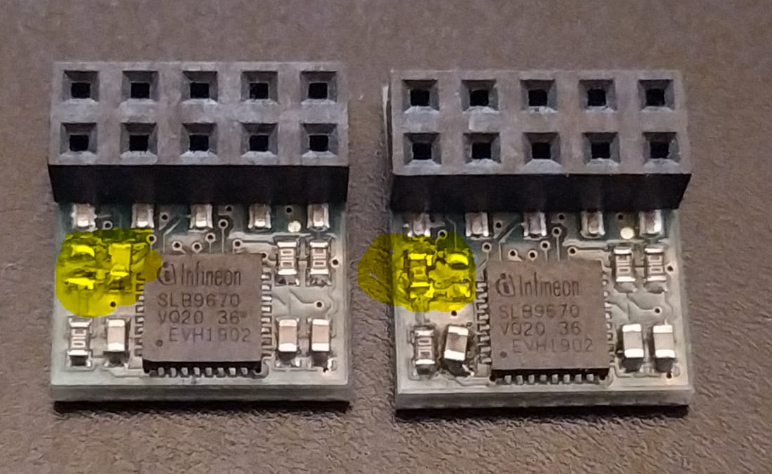
- Infineon Optiga™ SLB 9672 TPM 2.0 FW15.23
- TCG Spec 2.0 Rev. 01.51
- USB 2.0 to SPI Bridge based on CY7C65211A
- Compatible with libusb
- Own USB VendorID/ProductID
- Tested with https://github.com/tpm2-software/
- available TCTI-Driver in tpm2_tss for plug & play usage [2]
- 2 LEDs, one for "USB-RX/TX action" and one connected to a TPM-GPIO for user feedback
- Transparent ABS housing for the PCB
- LetsTrust-TPM2Go was designed, manufactured, and tested in Bavaria, Germany.
Preorders are now open, and you can find LetsTrust-TPM2Go here: https://buyzero.de/products/letstrust-tpm2go
With the promo code TPMDEV2023, you'll get a 7€ discount on the first stick. This code is active till the end of August.
The first batch is manufactured, updated and tested.
The estimated shipment date is the end of July/beginning of August at the latest.
(We are waiting for the updated Vendor ID list on www.usb.org/developers, as this final lists Pi3g as a vendor with the given number, I could finalise the sticks (I want to avoid to scrapping several 1000€s for a potential typo))
usb.org updated the list:
https://usb.org/sites/default/files/usb_vids_080223.pdf
Shipment will start next week! \o/
Bye for now!
Paul
[1] I could interact with these sticks over WSL2 on Windows 10, but without a d-bus and the abrmd only simple commands are functional .
.
[2] https://github.com/tpm2-software/tpm2-tss/blob/master/doc/tcti-spi-ltt2go.md
"More Hardware: LetsTrust-TPM2Go " vollständig lesen
Finally shipped to the stock \o/.

I hope, you will find this USB-Stick useful for your development!
Bye,
Paul
2023 August 2nd,
Update:
Shipment will start next week! \o/
Hello and welcome back,
Today, I would like to introduce my new product: LetsTrust-TPM2Go!
LetsTrust-TPM2Go is a USB 2.0 stick with a built-in TPM. It is designed to be compatible with Linux PCs or single-board computers that have USB-A ports (probably macOS but I could not test it). This product's main purpose is to simplify application development with TPM support. It can also be used if your embedded device is not ready or only has free USB ports on your target device.
Windows 11: LetsTrust-TPM2Go USB Stick is NOT compatible with Microsoft Windows 11 TPM 2.0 requirement!
Windows 10: LetsTrust-TPM2Go is not compatible [1].
Features:
- Infineon Optiga™ SLB 9672 TPM 2.0 FW15.23
- TCG Spec 2.0 Rev. 01.51
- USB 2.0 to SPI Bridge based on CY7C65211A
- Compatible with libusb
- Own USB VendorID/ProductID
- Tested with https://github.com/tpm2-software/
- available TCTI-Driver in tpm2_tss for plug & play usage [2]
- 2 LEDs, one for "USB-RX/TX action" and one connected to a TPM-GPIO for user feedback
- Transparent ABS housing for the PCB
- LetsTrust-TPM2Go was designed, manufactured, and tested in Bavaria, Germany.
Preorders are now open, and you can find LetsTrust-TPM2Go here: https://buyzero.de/products/letstrust-tpm2go
With the promo code TPMDEV2023, you'll get a 7€ discount on the first stick. This code is active till the end of August.
The first batch is manufactured, updated and tested.
(We are waiting for the updated Vendor ID list on www.usb.org/developers, as this final lists Pi3g as a vendor with the given number, I could finalise the sticks (I want to avoid to scrapping several 1000€s for a potential typo))
usb.org updated the list:
https://usb.org/sites/default/files/usb_vids_080223.pdf
Shipment will start next week! \o/
Bye for now!
Paul
[1] I could interact with these sticks over WSL2 on Windows 10, but without a d-bus and the abrmd only simple commands are functional
[2] https://github.com/tpm2-software/tpm2-tss/blob/master/doc/tcti-spi-ltt2go.md
"More Hardware: LetsTrust-TPM2Go " vollständig lesen