Hi,
today I will share with you some thoughts, insights, and statistics about LetsTrust-TPMs.
Let's start with the thoughts:
A "coincidence" led me into TPM Onchip development in 2016, where I met some TPM-addicted people, including one of my best friends today, Peter H.
Another "coincidence" introduced Peter to Max. Max, at that time, had become one of the first Approved Raspberry Pi resellers in the DACH region with Pi3g.com and his shop buyzero.de.
The path was short, and that's how I got to know Max. Thank you Peter!
The pitch was prepared, why Max should include my "prototype" in his shop... after a long preparation, the meeting took less than five minutes, and then it was already over. After that, we had a nice evening in his company

.
The Insights:
LetsTrust officially started on May 18, 2017, with the partnership between LetsTrust and Pi3g.com and a batch of 100 LetsTrust-TPM units. It was my first product, and for Max, it was a unique selling point since he was the only one offering discrete TPMs for the Raspberry Pi.
My disappointment in the first weeks grew, and the sales figures were almost non-existent.
Anyway, after 18 months, a trend became apparent, and it slowly approached one unit per day.
Four years after the start, the sales figures settled at around 300 units per quarter. (Yeah!)
Then came the chip crisis, impacting the availability of Raspberry Pis and, consequently, the sales of LT-TPM. The subsequent pandemic, which partly fueled the chip crisis, didn't help growth, but there wasn't a significant downturn either.
What I'm proud of: Through good foresight planning, we could consistently deliver from the first day of sales until today.
Raspberry Pis are available again, and this is noticeably boosting LT-TPM sales. Through this continuous growth, I could develop additional hardware, including:
- a ComputeModule3 board with USB/Ethernet/CAN/RS485/RS232/HDMI/TPM
- the first Raspberry Pi Breakoutboard for the BME688
- a Breakoutboard for an excellent CO2 sensor (stable CO2 measure for more than 5 years!)
- and of course, the LetsTrust-TPM2Go.
- Several more designs are in progress (so much to prototype, route and test).
And all of this started with a TPM on a small board.
However, it grew and became significant only through you and the community.
At this point, Dimitar Tomov should also be mentioned; he is the founder of
www.tpm.dev and undoubtedly contributed to LetsTrust's visibility.
Now, a few numbers and statistics!
Max kindly provided some anonymized data for this post.
A World Map!
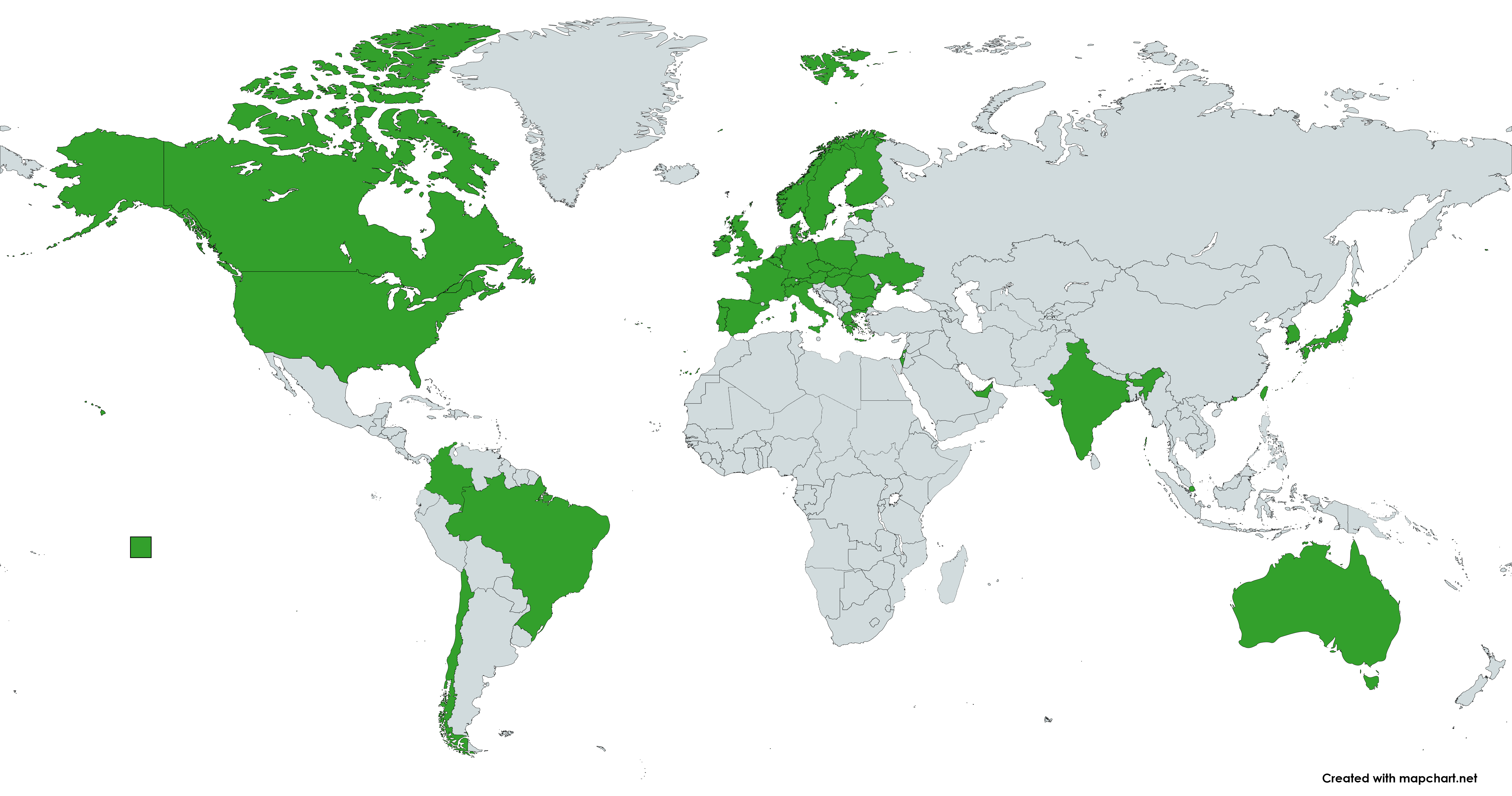
LetsTrust-TPMs have been shipped directly from Germany to 38 countries. Australia, Chile, and Japan seem to be the farthest distances covered. This list is derived from direct sales; if your country is missing, you probably ordered through a distributor.
Growth and Quantity Graph!
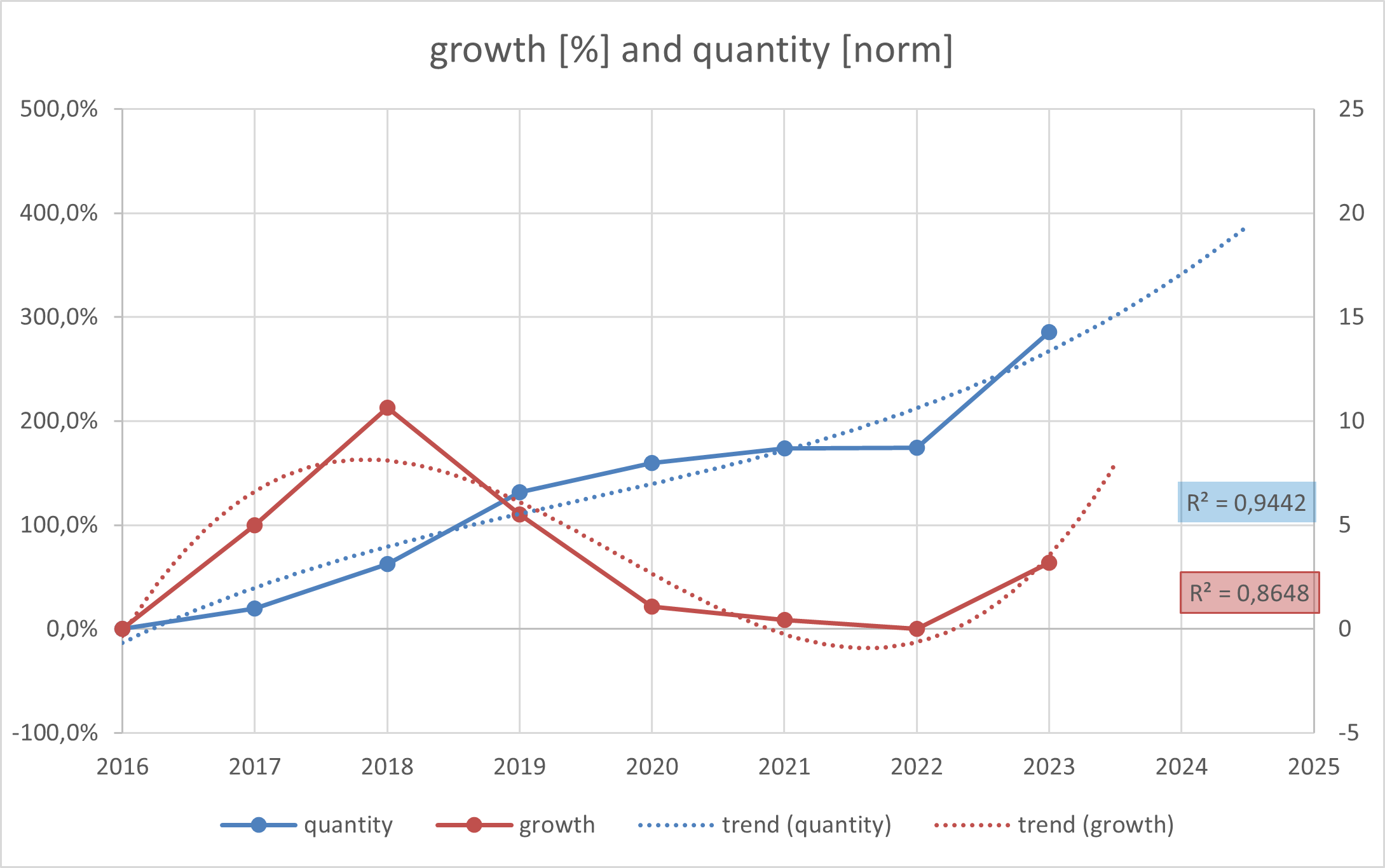
The blue graph shows that despite the pandemic and chip crisis, we managed to maintain annual sales at a good level. The orange graph looks quite similar to the hype cycle ^_^, so fingers crossed as it seems to be on an upward trend now!
I can tell you: You don't get rich with this project (at least not yet), but I have fun, and my wife occasionally gets flowers and you get sometimes new hardware designs.
See you soon!
Paul